- #_shellntel Cybersecurity Blog
- Posts
- Hash Master 1000 Version 2.0
Hash Master 1000 Version 2.0
Tool Drop from Wild West Hackin' Fest Mile High
I was fortunate to be selected as a speaker at the Mile High (Denver) Wild West Hackin’ Fest 2026 and this blog coincides with my talk this afternoon. I’ll be releasing Hash Master 1000 version 2.0 (free), a project I originally built because I was tired of stitching together scripts, spreadsheets, and screenshots during Active Directory password assessments.
Our industry has excellent password cracking tools. Hashcat is phenomenal, and with the right hardware it can produce incredible results. Where things tend to fall apart is everything that comes after cracking. Analysis is often shallow, reporting is inconsistent, and historical context is usually missing altogether. Too many assessments stop at “top passwords” and never dig into how users actually choose passwords, where systemic issues exist, or how environments change over time. Hash Master 1000 was built to close that gap.
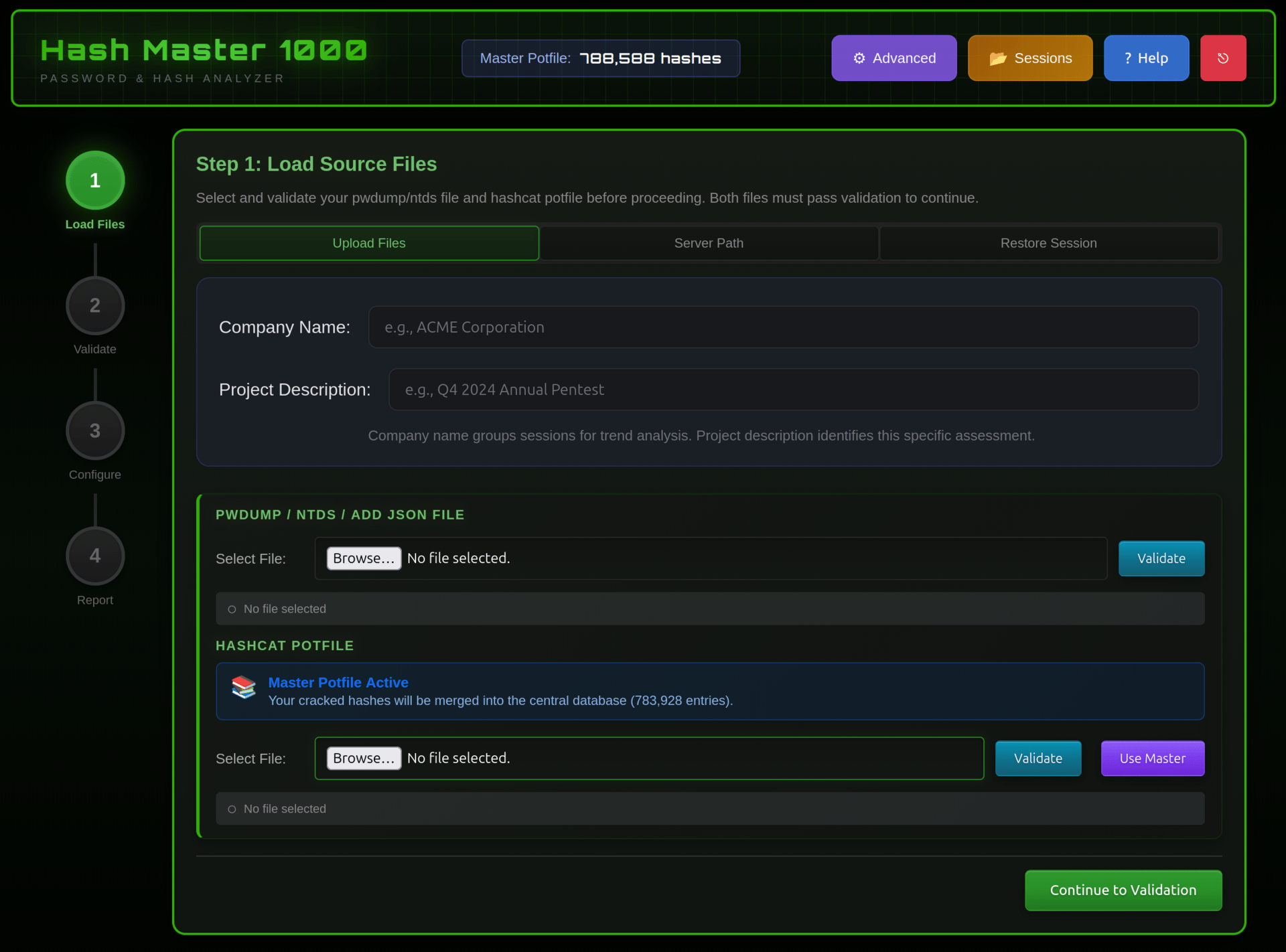
Hash Master 1000: Step 1 - Import Source Files
Hash Master 1000 is Active Directory focused and designed around how real AD password assessments are performed. It ingests pwdump, VSS, DCSync, or enriched ADD (SynerComm’s new Active Directory Dumper format) data along with a hashcat potfile and turns them into structured, meaningful analysis. Policy failures, password reuse, weak patterns, dictionary words, repeating substrings, common pitfalls and bad practices, it’s all there, and it’s all designed to be explored and exported.

Policy Violation: Accounts Failing Minimum Password Length
What’s New in Version 2.0
Version 2.0 significantly expands that capability. Session management allows assessments to be saved, restored, and compared. Trend analysis makes it possible to show whether an organization is improving or regressing over time. Kerberoast and AS-REP exposure analysis are integrated directly into the workflow, prioritizing accounts based on real operational risk instead of just theoretical vulnerability.
Quickly spot at risk privileged accounts with reused and cracked passwords, as well as accounts storing weak LM hashes.

A new password history analysis even identifies and highlights predictable rotation patterns detected in account passwords and hashes.

Password predictability shows how easily some user’s next password could be guessed
Perhaps the most helpful new feature is the ability to anonymously compare your uncracked NT hashes against the current Have I Been Pwned database of breached passwords. This is just one of several analysis reports than can be run without the need for cracking.

Anonymously compare NT hashes to Have I Been Pwned
A bleeding edge new feature in v2.0 is Advanced AI Analysis (AAIA). This feature is intentionally experimental, but it is already proving useful. Using local Ollama models, Hash Master 1000 can assist with pattern recognition, risk summarization, and narrative generation. Everything runs on infrastructure you control, and the output is designed to support analysts, not replace them. It’s clear that AI will play a significant role in how we analyze and report on password data going forward, and this is an early but practical step in that direction.

Screenshot: Hash Master 1000 - Report Sections

Screenshot: Hash Master 1000 - Advanced AI Analysis
Real AI Insights
One of the more interesting things I’ve observed while using Advanced AI Analysis is how quickly it can surface context that isn’t obvious from charts alone. In several assessments, I’ve asked AI to infer the likely industry, geographic region, or even the name of the organization based solely on cracked passwords. Users gravitate toward what’s familiar, internal project names, business terms, city names, regional sports teams, and cultural references all leak through in password choices. In more than one case, AI was able to make surprisingly accurate guesses about a company’s name, location, or line of business without being given any external information.
Another practical insight has been how limited English-only dictionary cracking really is for many environments. AI has helped identify names, words, and concepts embedded in passwords that don’t appear in standard English wordlists, terms rooted in other languages, cultures, and naming conventions. That recognition has directly influenced how we build custom wordlists and attack strategies, especially for organizations with a global footprint. These aren’t theoretical ideas, they’re insights that translate into better cracking methods and more accurate reporting.
Hash Master 1000 is Free to Use
Hash Master 1000 is free to use by the security community and the source code is available. That wasn’t an afterthought. Tools shape how assessments are performed, and better tools lead to better testing. Making it public invites scrutiny, contributions, and improvement from people who are actually doing the work.
At the end of the day, Hash Master 1000 isn’t trying to replace cracking rigs or magically crack more passwords. It’s a force multiplier. It helps turn raw cracking output into insight that testers can stand behind and organizations can act on. Hash Master 1000 may just be the Swiss Army knife for AD password and hash analysis.